
StegoHunt MP is the next generation of WetStone’s industry-leading steganography program detection tool and steganalysis suite. StegoHunt effectively detects the presence of both steganography and data hiding programs as well as the files in which the data payload may have been hidden (carrier files).
StegoHunt MP’s new modern codebase improves upon the previous version of StegoHunt, giving users exciting new features.
These features include:
- Expanded filetype support
- Enhanced reporting, including HTML and CSV reports
- Configurable data appending thresholds
- Hash file generation supports efficient re-scanning of suspect systems to detect steganography and encryption programs
- Suspicious Files archive to quickly access files identified in the StegoHunt MP report
- Extraction of image files from other files, including Office documents and PDFs
- Additional archive filetypes supported
- Improved statistical analysis checks to reduce false positives and improve detection capabilities
- User option to whitelist files and exclude them from a report if determined to be a false positive
- Modern codebase allows for quicker turnaround on product enhancements and higher performance compared to the legacy version of StegoHunt
- Factory-provided whitelists improve scanning performance and reduce false positives for files known to originate from reputable sources, such as operating system files and popular applications
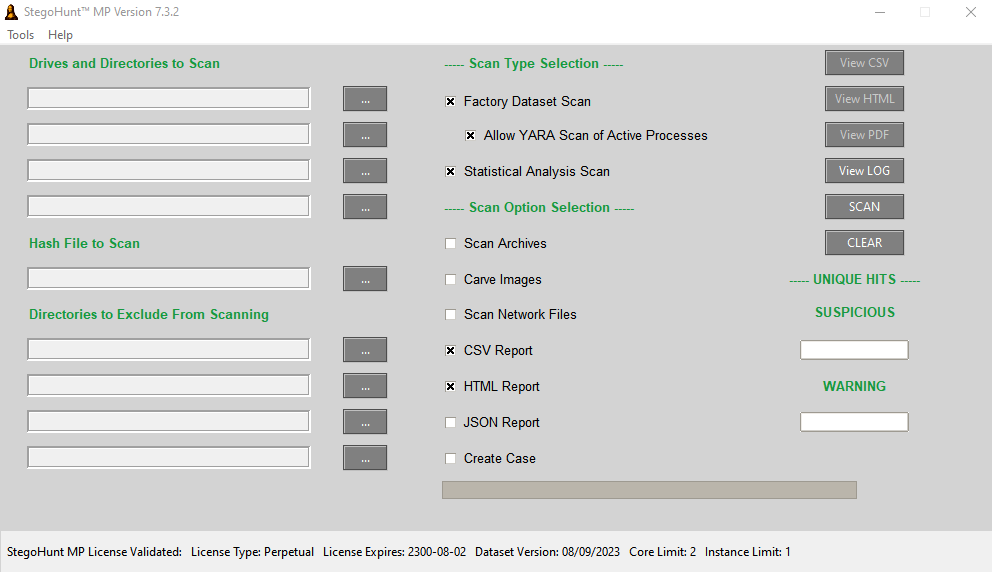
Cyber criminals are becoming increasingly proficient at covering their tracks and hiding incriminating information. There are currently over a thousand known tools for hiding data within images, audio files, digital video, network protocols, and other types of digital carriers. It has never been more important to discover these data hiding methods and the artifacts that data hiding tools can leave behind on a system. Recently, malware developers have been actively integrating data hiding capabilities into malicious code to create a form of advanced persistent threat (APT), known as fileless malware. An analysis performed by McAfee Labs on the malware attack that occurred during the 2018 PyeongChang Olympics revealed a malicious PowerShell script embedded in an image within a Microsoft Word document. This malicious script began execution when a user opened the Word document containing the image. With StegoHunt MP, investigators have the ability to identify images that may contain potentially malicious or sensitive information, and leverage WetStone’s steganalysis tools to further investigate the embedded data.
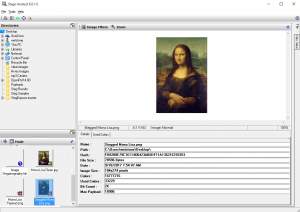
After potential carrier files have been identified by StegoHunt MP, digital forensic analysts can advance the investigation by leveraging the powerful analytical capabilities of StegoAnalyst to view important characteristics of the carrier file. Steganalysis techniques, such as viewing file attributes, discrete cosine transform (DCT) coefficients and RGB color values provide clues that the investigator can use to identify the data hiding method being employed.
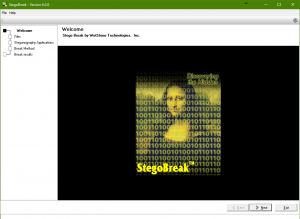
StegoBreak provides digital investigators with a tool to help break the encryption used by many data hiding programs. StegoBreak will launch a dictionary attack against the encryption and, if successful, allow the investigator to view the payload.
FEATURES OF STEGOHUNT™ MP
- Identify the presence of carrier files on a system through statistical analysis techniques
- Identify the presence of data hiding tools and artifacts on a system
- View data about images, such as the bitmap, and utilize color filters for more information
- Crack and extract payloads from carrier files using encryption by launching a dictionary attack against the data hiding password
- Comprehensive reporting
- Compatible with a variety of Windows desktop and server platforms:
- Windows 7
- Windows 8
- Windows 8.1
- Windows 10
- Windows Server 2008 and 2008 R2
- Windows Server 2012 and 2012 R2
- Windows Server 2016
- Windows Server 2019
FILE TYPES SUPPORTED BY STEGOHUNT™ MP
- JPEG
- BMP
- GIF
- PNG
- WAV
- MP3
- JPEG 2000
- TIFF
- PCX
- 3GP
- M4V
- 7z
- M4A
- MOV
- MP4
- AVI
- FLV
- MPG
- ASF
- OLE (.doc, .ppt, .xls, etc)
- Office files (.docx, .pptx, .xlsx, etc)
- ZIP
- TAR
INCLUDED IN THIS SUITE OF TOOLS:
StegoHunt™MP
- Quickly identify if steganography is present in your investigations by scanning for thousands of steganography, stegware and data hiding applications using advanced, fast search methods
- Identify suspect carrier files that otherwise go undetected, including program artifacts, program signatures, and statistical anomalies
- Generate case-specific reports for management or court presentation
- Utilize multiple operational discovery modes, including directory, drive, archives, drive image, and network path
StegoAnalyst™
- Steganography analysis tool that provides deep investigation of detected images and audio files
- Utilize the file viewing panel to display the individual file attributes, including image details, discrete cosine transform (DCT) coefficients, and color pairs
- Select from various filter options for further presentation and analysis, such as least significant bit (LSB) of specific colors.
StegoBreak™
- Quickly and easily crack and extract payloads from many carrier files using a simple point and click interface
- Leverage the popular password dictionaries included in order to execute a dictionary attack
- Easily bring in other dictionaries, as well as create your own, to expand your dictionary attack
DELIVERABLE
- Your choice of either Electronic Software Download (ESD) or USB Flash Drive (Flash) license type
- Access to monthly Dataset updates
- Customer support portal account
- 1-Year maintenance
LICENSING TYPES
- ESD: Electronic software download for use on a single system. Available as a subscription license. Not transferable. Basic license is 2 cores, additional core licensing available.
- FLASH: 16GB USB 3.0 device for use in field investigations, and on multiple systems. Limited to 2 cores.
Schedule a Demonstration
